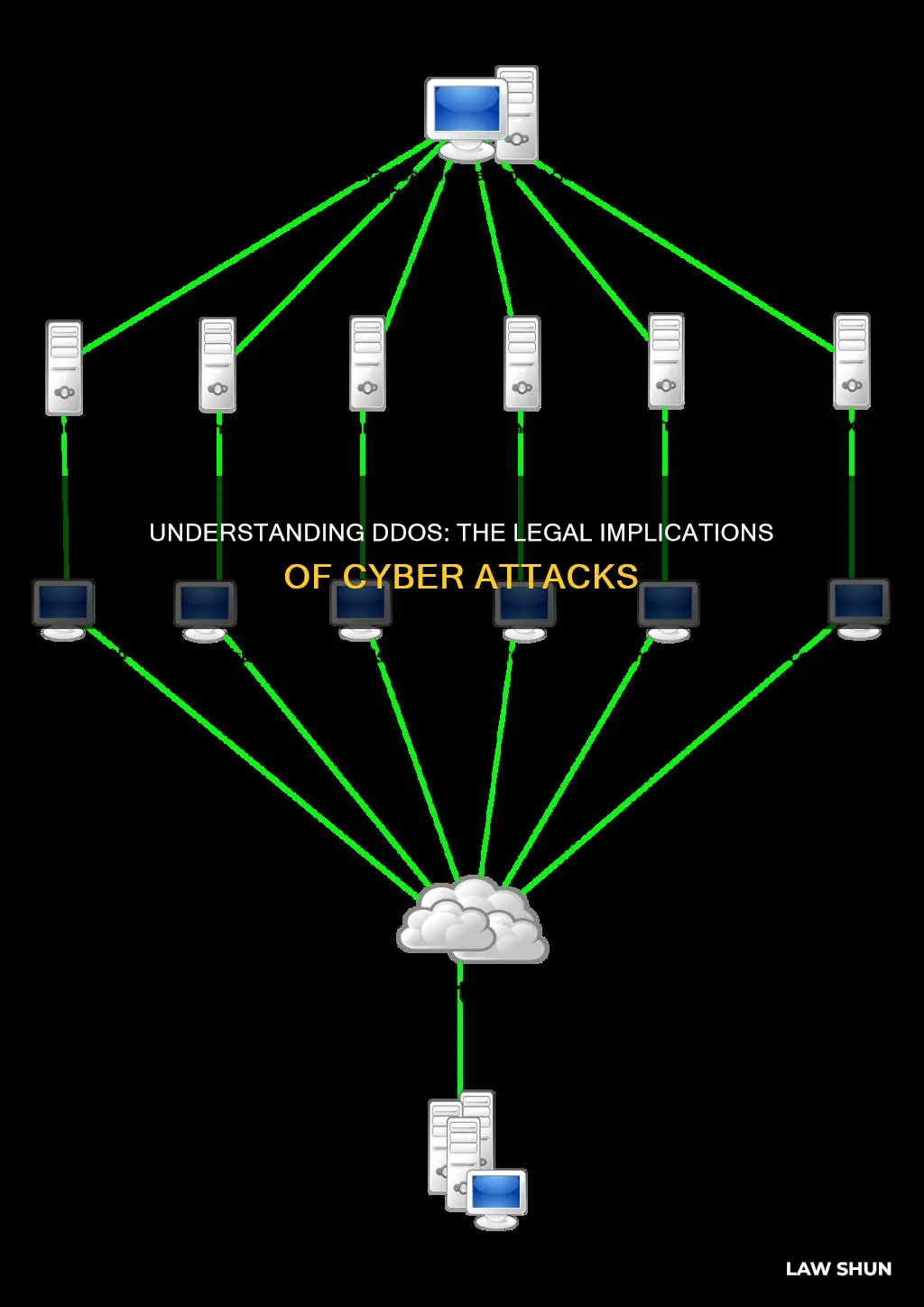
DDoS (Distributed Denial of Service) attacks are a serious cyber threat that can disrupt online services and networks. These attacks involve flooding a target system with a massive amount of internet traffic, making it impossible for legitimate users to access the service. The question of what laws DDoS attacks break is crucial, as these actions can have severe legal consequences. DDoS attacks can violate various laws, including those related to computer fraud, cybercrime, and even terrorism, depending on the context and intent of the attack. Understanding the legal implications of DDoS attacks is essential for both individuals and organizations to protect themselves and ensure a safe online environment.
What You'll Learn
- Denial of Service: DDoS attacks overwhelm networks, disrupting legitimate traffic and services
- Network Congestion: Intentionally causing network congestion to block legitimate users
- Resource Exhaustion: Exhausting server resources, rendering them unable to handle normal traffic
- Service Disruption: Intentionally disrupting online services, causing downtime and loss of revenue
- Violation of Terms of Service: DDoS attacks often violate terms of service, leading to legal consequences

Denial of Service: DDoS attacks overwhelm networks, disrupting legitimate traffic and services
Denial of Service (DoS) attacks and Distributed Denial of Service (DDoS) attacks are malicious actions that aim to disrupt the normal functioning of computer networks and services. These attacks can have severe consequences, causing significant financial losses, data breaches, and service disruptions for individuals, organizations, and even entire infrastructures. Understanding the legal implications of DDoS attacks is crucial to combat this growing cyber threat.
When a DDoS attack occurs, the attacker floods a target network or server with an overwhelming amount of traffic, rendering it unable to handle legitimate user requests. This is achieved by utilizing multiple compromised devices, often infected with malware, to generate a massive volume of requests simultaneously. The primary goal is to overload the target's resources, such as bandwidth, memory, or processing power, until it becomes unresponsive or crashes. As a result, legitimate users are denied access to the affected services, causing a denial of service.
From a legal perspective, DDoS attacks can violate several laws and regulations, depending on the jurisdiction and the specific circumstances of the attack. Firstly, DDoS attacks can be considered a form of computer fraud or abuse under various legal frameworks. For example, in the United States, the Computer Fraud and Abuse Act (CFAA) prohibits unauthorized access to computer systems and networks, which can encompass DDoS attacks that exceed the system's capacity. Similarly, in the European Union, the Directive on Security of Network and Information Systems (NIS Directive) requires member states to protect against cyber threats, including DDoS attacks, that could significantly impact critical services.
The impact of DDoS attacks can be far-reaching, affecting not only the immediate target but also the broader network infrastructure. These attacks can disrupt online services, financial transactions, communication networks, and even critical infrastructure. As such, they can lead to significant financial losses, service interruptions, and potential harm to individuals and organizations. In many jurisdictions, causing such disruptions and damage to computer systems and networks is a criminal offense, and perpetrators can face legal consequences, including fines and imprisonment.
Furthermore, DDoS attacks can be linked to other illegal activities, such as cyber espionage, political activism, or financial gain. For instance, attackers may use DDoS attacks as a distraction or cover for other malicious activities, such as data theft or unauthorized access. In these cases, the legal implications can be more severe, involving additional charges related to data breaches, privacy violations, or other cybercrimes. It is essential for law enforcement agencies and cybersecurity professionals to collaborate in identifying and prosecuting DDoS attack perpetrators to ensure a robust legal response to this evolving threat.
Andrew Carnegie: Lawbreaker or Law-Abiding?
You may want to see also

Network Congestion: Intentionally causing network congestion to block legitimate users
When an attacker intentionally causes network congestion, they are essentially engaging in a form of denial-of-service (DoS) attack, but with a twist. While a traditional DoS attack aims to make a target server or service unavailable, network congestion attacks focus on the network itself. By generating a large volume of traffic or using specific techniques to exploit network vulnerabilities, attackers can slow down or even halt the data flow within the network. This disruption can affect multiple users and services, not just a single target.
The impact of such attacks can be far-reaching. Legitimate users may experience slow internet speeds, frequent disconnections, or complete inability to access online services. This can result in significant financial losses for businesses, disruption of critical services, and even potential safety hazards in certain contexts, such as healthcare or emergency response systems. Network congestion attacks are particularly insidious because they can be challenging to detect and mitigate, often requiring specialized tools and expertise.
From a legal perspective, intentionally causing network congestion can be considered a violation of computer fraud and abuse laws in many jurisdictions. These laws are designed to protect computer systems and networks from unauthorized access, damage, and misuse. By causing congestion, attackers can be seen as engaging in activities that interfere with the normal operation of computer systems, which is a clear violation of these laws. Additionally, such actions may also be subject to telecommunications laws and regulations, which further emphasize the importance of maintaining the integrity and reliability of network infrastructure.
In summary, network congestion attacks are a sophisticated form of cyber-attack that can have severe consequences. They disrupt the normal functioning of networks, causing legitimate users to suffer. Legally, these actions can be prosecuted under computer fraud and abuse laws, and they may also attract attention from telecommunications authorities. Understanding and addressing these attacks is crucial to ensure the security and reliability of network infrastructure and protect the interests of all users.
The House: Lawbreakers or Law Abiders?
You may want to see also

Resource Exhaustion: Exhausting server resources, rendering them unable to handle normal traffic
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks are malicious activities that aim to disrupt the normal functioning of a network, server, or online service. One of the primary techniques employed in these attacks is resource exhaustion, which can have severe legal implications. When a DDoS attack targets a server, its primary objective is to overload the server's resources, rendering it unable to handle legitimate user requests. This is achieved through a flood of traffic, often generated by a network of compromised computers or devices, known as a botnet.
Resource exhaustion attacks can take several forms, all aimed at depleting the server's capacity to process requests. One common method is the volumetric attack, where the attacker sends a massive amount of data to the target server, overwhelming its bandwidth and network resources. This flood of traffic can be directed at the server's IP address or specific ports, making it difficult for the server to distinguish between legitimate and malicious requests. As a result, the server's resources, including memory, processing power, and network interfaces, become saturated, leading to a complete denial of service.
Another approach is the application layer attack, which targets specific functions or services provided by the server. Attackers may send a large number of requests to a particular web page or API endpoint, causing the server to exhaust its resources while processing these requests. For example, a GET request flood to a web server's homepage can quickly consume its available memory and processing power, rendering it unable to respond to other user requests. This type of attack is often more sophisticated and harder to detect, as it may not involve an overwhelming amount of traffic but rather a series of well-crafted, resource-intensive requests.
The impact of resource exhaustion attacks can be devastating. When a server is rendered unable to handle normal traffic, legitimate users are denied access to essential services, such as online banking, e-commerce platforms, or critical infrastructure systems. This disruption can lead to significant financial losses, reputational damage, and even legal consequences for the affected organizations. In many jurisdictions, causing harm to computer systems or networks, including resource exhaustion attacks, can be considered a criminal offense, resulting in fines and imprisonment.
To mitigate the impact of DDoS attacks and resource exhaustion, organizations should implement robust security measures. This includes using network monitoring tools to detect unusual traffic patterns, employing traffic filtering and rate-limiting techniques, and investing in DDoS mitigation services offered by cloud service providers. Additionally, organizations should regularly update their security protocols and educate their staff about the risks and best practices associated with DDoS attacks. By taking proactive measures, businesses can ensure the availability and resilience of their online services, even in the face of such malicious activities.
Breaking Logic's Laws: A Guide to Unconventional Reasoning
You may want to see also

Service Disruption: Intentionally disrupting online services, causing downtime and loss of revenue
The act of intentionally disrupting online services through Distributed Denial of Service (DDoS) attacks can have significant legal implications and is considered a serious offense in many jurisdictions. DDoS attacks are designed to overload a target's network infrastructure, rendering it unable to handle legitimate user requests and causing service disruption. This disruption can lead to financial losses, data breaches, and reputational damage for the affected organizations.
When it comes to the legal aspects, DDoS attacks can violate several laws, depending on the country and the specific circumstances of the attack. Firstly, it is essential to understand that DDoS attacks are often used as a tool for cybercrime. The primary goal is to gain unauthorized access to computer systems, steal sensitive information, or disrupt critical infrastructure. From a legal standpoint, these actions can be categorized as computer fraud, data theft, or even cyber terrorism in some cases.
In many countries, computer fraud is a criminal offense, and DDoS attacks can be considered a form of fraud as they involve the intentional manipulation of computer systems to gain unauthorized access or disrupt services. The legal consequences for such actions can include fines, imprisonment, or both. For instance, in the United States, the Computer Fraud and Abuse Act (CFAA) prohibits unauthorized access to computer systems and can be applied to DDoS attacks, leading to severe penalties. Similarly, the UK's Computer Misuse Act (CMA) and Australia's Computer Fraud Act also address such cybercrimes.
Furthermore, DDoS attacks can result in significant financial losses for businesses and organizations. The downtime caused by these attacks can lead to lost revenue, decreased productivity, and increased operational costs. In some cases, companies may also face legal action from affected customers or partners seeking compensation for the disruption. This aspect of service disruption can be particularly damaging to online businesses, e-commerce platforms, and financial institutions, which heavily rely on uninterrupted online services.
To combat DDoS attacks and protect online services, organizations must implement robust cybersecurity measures. This includes network monitoring, traffic analysis, and the use of DDoS mitigation services. By understanding the legal implications and taking proactive steps, businesses can safeguard their online presence and ensure compliance with relevant laws. It is crucial to remember that DDoS attacks are not just technical issues but also potential criminal activities with serious legal consequences.
Ignorance of the Law: What Are the Consequences?
You may want to see also

Violation of Terms of Service: DDoS attacks often violate terms of service, leading to legal consequences
DDoS (Distributed Denial of Service) attacks are a serious violation of the terms of service (ToS) for many online platforms and networks. These attacks involve flooding a target server or network with a massive amount of traffic, rendering it unable to handle legitimate user requests. When individuals or groups engage in DDoS attacks, they are essentially disrupting the intended use of a service, which is a clear breach of the agreed-upon rules and regulations set by the service provider.
The terms of service for various online services, including websites, gaming platforms, and cloud computing providers, explicitly prohibit activities that could lead to a denial of service. These ToS documents are legally binding contracts between the service provider and its users. By launching a DDoS attack, attackers are violating these contracts, as they are causing a disruption that goes against the very nature of the service being offered.
The legal consequences of such violations can be severe. Service providers have the right to take action against those who engage in DDoS attacks, and this can result in legal repercussions for the attackers. In many jurisdictions, DDoS attacks are considered a form of cybercrime, and those involved can face criminal charges. These charges may include computer fraud, conspiracy, or even more severe offenses depending on the scale and impact of the attack.
Furthermore, the legal implications can extend beyond criminal prosecution. Victims of DDoS attacks can sue the attackers for damages, seeking compensation for the financial losses incurred due to the disruption of their services. Lawsuits may also be filed to recover any costs associated with mitigating the attack, restoring services, and investigating the incident.
It is important for individuals and organizations to understand that engaging in DDoS attacks is not only unethical but also illegal. The potential legal consequences can be far-reaching, including criminal penalties and civil lawsuits. By adhering to the terms of service and respecting the rights of others, users can help maintain a fair and secure online environment.
Asylum Seekers: Central American Migration and Legalities
You may want to see also
Frequently asked questions
DDoS stands for Distributed Denial of Service. It is a type of cyber attack where multiple compromised computer systems flood a target network or server with traffic, making it unavailable to legitimate users.
DDoS attacks are illegal as they are designed to disrupt and disable computer systems, causing significant harm to individuals, organizations, and even entire infrastructures. These attacks can lead to financial losses, data breaches, and service disruptions, violating various laws and regulations related to computer fraud, network intrusion, and cybercrime.
DDoS attacks can violate several laws, including:
- Computer Fraud and Abuse Act (CFAA) in the United States, which prohibits unauthorized access and damage to protected computers.
- Cybercrime laws in various countries, which address online fraud, hacking, and the misuse of computer systems.
- Regulations on network security and infrastructure protection, ensuring the availability and integrity of critical systems.
Yes, DDoS attackers can face severe legal consequences. Law enforcement agencies work to identify and prosecute perpetrators, often with international cooperation due to the distributed nature of DDoS attacks. Offenders may be charged with crimes such as computer hacking, conspiracy, and causing damage to computer systems, which can result in fines and imprisonment.







